Security Information Write For Us
Security Information differs from cyber security in both scope and purpose. These two terms are often used interchangeably, but more precisely, cybersecurity is a subcategory of information security. Information security is a broad field that includes many areas, such as physical security, termination security, data encoding, and network security. It is also carefully related to information assurance, protecting information from threats such as natural tragedies and server failures.
Cybersecurity primarily addresses technology-related threats, with practices and tools that can prevent or mitigate those threats. Another related category is data security, which focuses on protecting an organization’s data from accidental or malicious exposure by unauthorized parties.
Information Security Policy
An Information Security Policy (ISP) is a set of rules that guide individuals using IT assets. Companies can create information security policies to ensure employees and other users follow security protocols and procedures. Security policies ensure that only authorized users can access sensitive systems and information.
Creating effective security policies and ensuring compliance are essential to preventing and mitigating security threats. To make your policies truly effective, update them regularly based on company changes, new threats, conclusions drawn from previous breaches, and changes to security systems and tools.
Make your information security strategy practical and sensible. Necessities of various departments within an organization, it is necessary to implement an exception system with an approval process that allows departments or individuals to deviate from the rules in certain circumstances.
Information Security Threats
There are hundreds of information security threat categories and millions of known threat vectors. Below, we discuss some of the key threats that security teams in modern enterprises prioritize.
Unsecured System
The speed and development of technology often lead to compromises in security measures. In other cases, systems are developed without security and remain operational as legacy systems. Organizations must identify these less secure systems and mitigate threats by securing, repairing, disabling, or isolating them.
Social Media Attacks
Many people have social media accounts, where they often inadvertently share much information about themselves. Attackers can launch attacks directly through social media, for example, by spreading malware through social media messages, or indirectly, by using information obtained from such sites to analyze user and organizational vulnerabilities and use it to design attacks.
Social Engineering
Social engineering involves attackers sending emails and messages that trick users into taking actions that could compromise their security or leak personal information. Attackers manipulate users using psychological triggers such as curiosity, urgency, or fear.
Because the source of a social engineering message appears trustworthy, people are more likely to comply, for example, by clicking on a link that installs malware on their premises or by providing personal information, credentials, or financial details.
How To Submit Your Articles?
To get your Blog posted on Techitags, you will first have to pitch us a post and showcase your writing skills and knowledge.
You can drop a mail at contact@techitags.com with the subsequent info
Why Write For Techitags – Security Information Write For Us
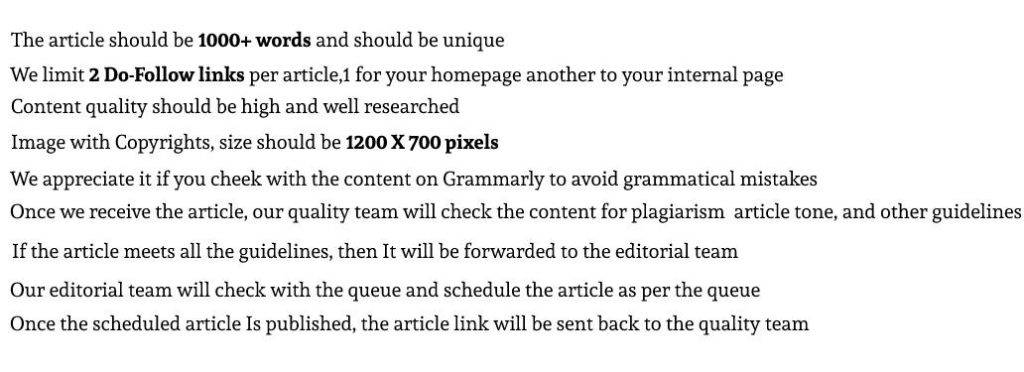
Guidelines For Blog Post
Search Terms Related To Security Information Write For Us
submit an article
contributor guidelines
become a guest blogger
guest posting guidelines
submit article
guest author
looking for guest posts
guest posts wanted
guest post
become guest writer
This post was written by
submit an article
send a tip
write for us
submit post
Search Terms Related To Security Information Write For Us
Security Information “guest post
Security Information “write for us”
Security Information “guest article”
Security Information “guest post opportunities”
Security Information “this is a guest post by”
Security Information “looking for guest posts”
Security Information “contributing writer”
Security Information “want to write for”
Security Information “submit blog post”
Security Information “contribute to our site”
Security Information “guest column”
Security Information “submit Face Book Ads”
Security Information “submit Face Book Ads”
Security Information “This post was written by”
Security Information “guest post courtesy of ”
Security Information “guest posting guidelines”
Security Information “suggest a post”
Security Information “submit an article”
Security Information “contributor guidelines”
Security Information “contributing writer”
Security Information “submit news”
Security Information “submit post”
Security Information “become a guest blogger
Security Information “guest blogger”
Security Information “guest posts wanted”
Security Information “guest posts wanted”
Security Information “guest poster wanted”
Security Information “accepting guest posts”
Security Information “writers wanted”
Security Information “articles wanted”
Security Information “become an author”
Security Information “become guest writer”
Security Information “become a contributor”
Security Information “submit guest post”
Security Information “submit an article”
Security Information “submit article”
Security Information “guest author”
Security Information “send a tip”
Security Information : “guest blogger”
Security Information : “guest post”
Related To Pages
Digital Marketing Write For Us
